What exactly is involved in cloud monitoring and how does it protect your organization from cyber threats? Learn more about this important service in the visual deep dive below, courtesy of Live Action:

Source: Live Action

What exactly is involved in cloud monitoring and how does it protect your organization from cyber threats? Learn more about this important service in the visual deep dive below, courtesy of Live Action:


In today’s complex realm of cyber defense, you’ve got to stay up on your game. Traditional protection methods are not enough – that’s why it is time to learn more about network detection and response – learn more in the visual deep dive below:


Data breaches are happening all over the globe. While it sometimes feels like this may not happen in your own organization, it’s important to keep on top of your cybersecurity. Learn more about global data breaches in the infographic below:

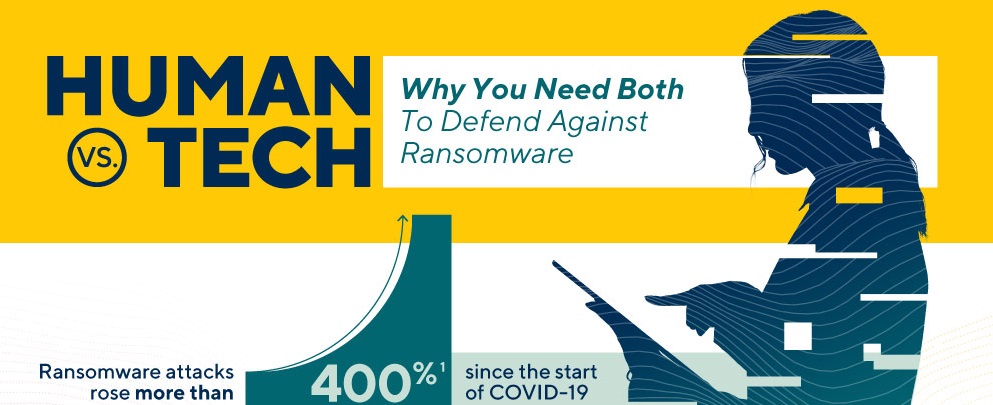
Ransomware has become a major threat, only exponentially accelerated by the remote workforce brought on by the global pandemic. It’s going to take some fancy footwork with humans and tech to stay ahead of cyber attacks. Learn how in the following infographic from Pondurance:


An incredible 85% of all email is spam. Much of this is just annoyance, but learn how to protect yourself in the infographic below, courtesy of Avanan.
![How Safe Are Your Emails? [infographic]](https://i0.wp.com/www.avanan.com/hubfs/website/img/infographics/How-Safe-Are-Your-Emails.jpg?w=450&ssl=1)
Courtesy of Avanan

And how does it help, you may wonder? It’s not a one size fits all solution, and a far cry from preventative measures. Still, it can save a bundle in coverage, payouts, and legal fees. Think you’re ready to have cyber insurance for your business? Read on to the infographic below:


What do basketball and cybersecurity have in common? More than you think. Whether you’re talking about a 3 point shot or a hacker’s attack vector, finding the hidden threat is everything. See more from Pondurance:


Now that over half of the American workforce had a taste of what it’s like to work remotely, working from home will become a standard for many. The question is – how will we keep up with cybersecurity?
Passwordless security is key – learn more in the infographic below:
